Comprehensive mobile data management suite to take danger out of BYOD
Now more than ever, many workers are choosing to use their own devices in a trend known in business circles as Bring Your Own Device (BYOD) to store and transfer data to and from their workplace. While this is convenient, especially for those employees who face a long commute or are constantly going to meetings, there are a few drawbacks, especially where security is concerned.
A suite to suit all companies?
Egnyte recently announced that they were to release a new suite where all company data stored on remote devices can be managed remotely. The Mobile Data Management Suite is packed with features designed to give companies complete control over where and how their data is stored on external mobile devices such as laptops, tablets and smartphones.
Among the features present in the suite are:
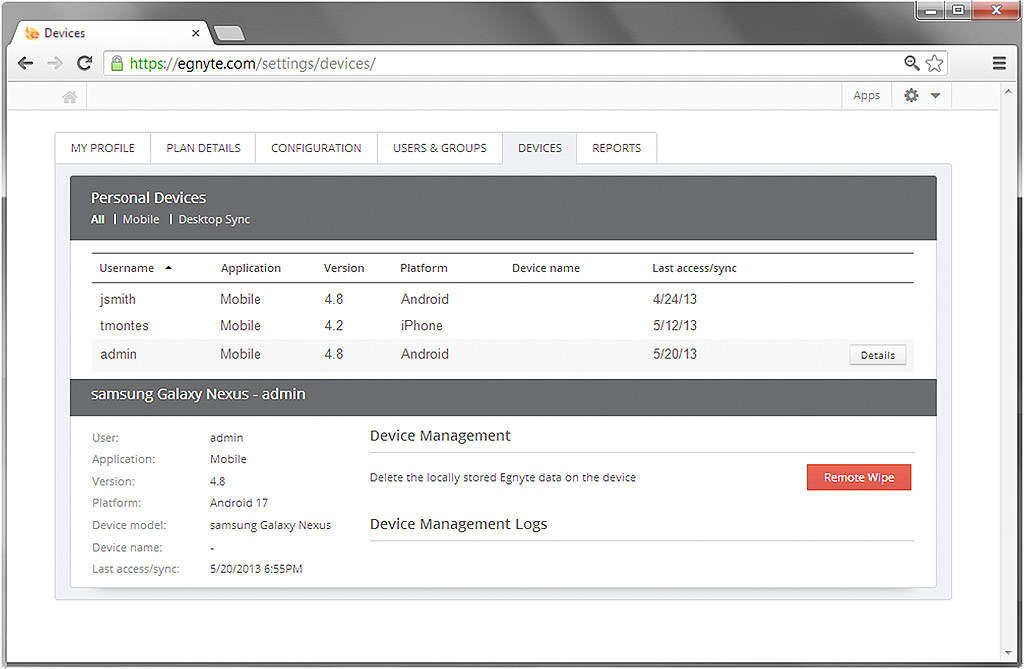
- A control panel from where different devices using the Egnyte account can be accessed monitored and, in the event where data or files are compromised, allow for a remote wipe to be performed. The remote wipe function can also be used in the event that a device is lost or stolen.
- Local file encryption – this can be used for smartphones and tablets, making files stored on them impenetrable.
- A two-step login verification facility. After entering the username and password, the account then has to be opened via a phone call or text message.
- Certificate-based device trust – only devices with the correct safety features can access an account.
Danger averted
The new suite is something all businesses that have a dedicated IT department could do benefit from. In using the suite, technicians’ jobs will be made a lot easier, plus the potential financial losses arising from lost or compromised data will be limited courtesy of being able to perform a remote wipe.
You can’t put a price on being able to control all your data. Even if many of your company’s employees bring their own devices to work, it’s possible to see what’s being done with each individual document and, perhaps more importantly from a security standpoint, who’s accessing them.